The unintentional, fraudulent outflow of data from an organisation poses a major challenge for the affected companies that goes beyond the immediate handling of the IT security incident. Data leaks in particular are very diverse and complex in their need for handling. They can also lead to immense financial and reputational damage.
Full disclosure and transparency are extremely important
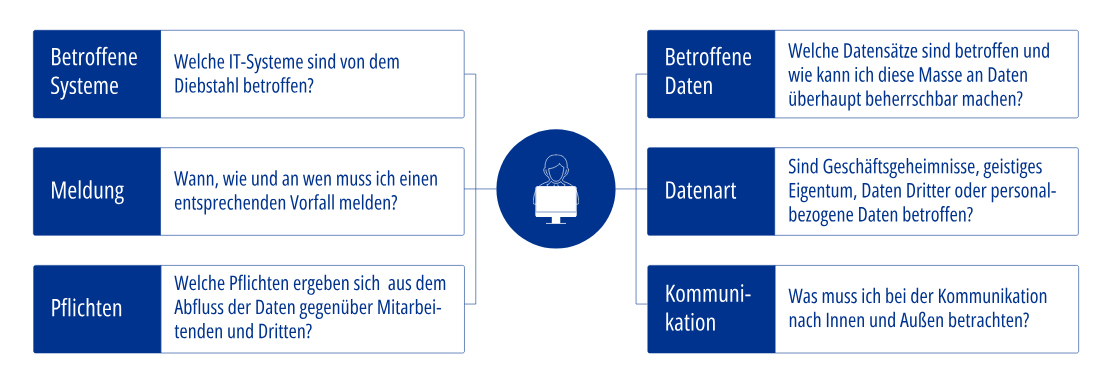
In order to minimise damage, it is extremely important to investigate such cyber attacks immediately and completely and to bring transparency to the incident. Immediate questions that arise include:
- What data was leaked in the first place?
- Have I lost company secrets, third-party data or personal data?
- Am I being blackmailed?
- What obligations do I have towards data subjects, third parties and supervisory authorities?
- Who do I need to involve internally and what processes need to be put in place?
Immediate questions in the event of data theft
Such an incident often results in further communication and information obligations for companies, which can involve considerable effort and the use of human and structural resources. The sheer volume of data and lack of knowledge about its content also often lead to great uncertainty and present companies with major technical challenges. Using tried-and-tested procedures and the latest technology (e.g. machine learning), the mountains of data can be made manageable.
Based on many years of practical experience, we not only support you in the clarification and complete elimination of the attack, the processing of the data leak and data content and ensure a secure restart of your business processes, but also accompany you in particular in the data protection law processing of the incident.
Our range of services
KPMG provides you with comprehensive support in investigating a cyber attack:
Your contacts
Michael Sauermann
Partner, Audit, Regulatory Advisory, Forensic
KPMG AG Wirtschaftsprüfungsgesellschaft
- Item 1
- Item 2


