October 2024
Cyber threats are some of the most severe and dynamic operational risks that European banks face. As the economy becomes ever more digitalised, the cyber challenge is only set to grow.
Bank know that the cyber environment is rapidly evolving, demanding significant effort to ensure cyber security can keep pace. Key factors driving the need for heightened focus on cyber resilience include:
The disruption of July 2024 has further sharpened banks’ focus on cyber and information and communication technology (ICT) risks. It also highlighted the potential vulnerabilities that arise from the industry’s growing use of third-party service providers in the technology sector. Regulators and supervisors are also concerned about banks’ dependence on third parties for the provision of core operational services. These concerns are heightened by high levels of concentration among technology providers and the risks that can arise from sub-contracting — illustrated by the recent impact on Microsoft’s services.
Third-party provider outages like those in July can create a range of pain points for banks spanning several areas.
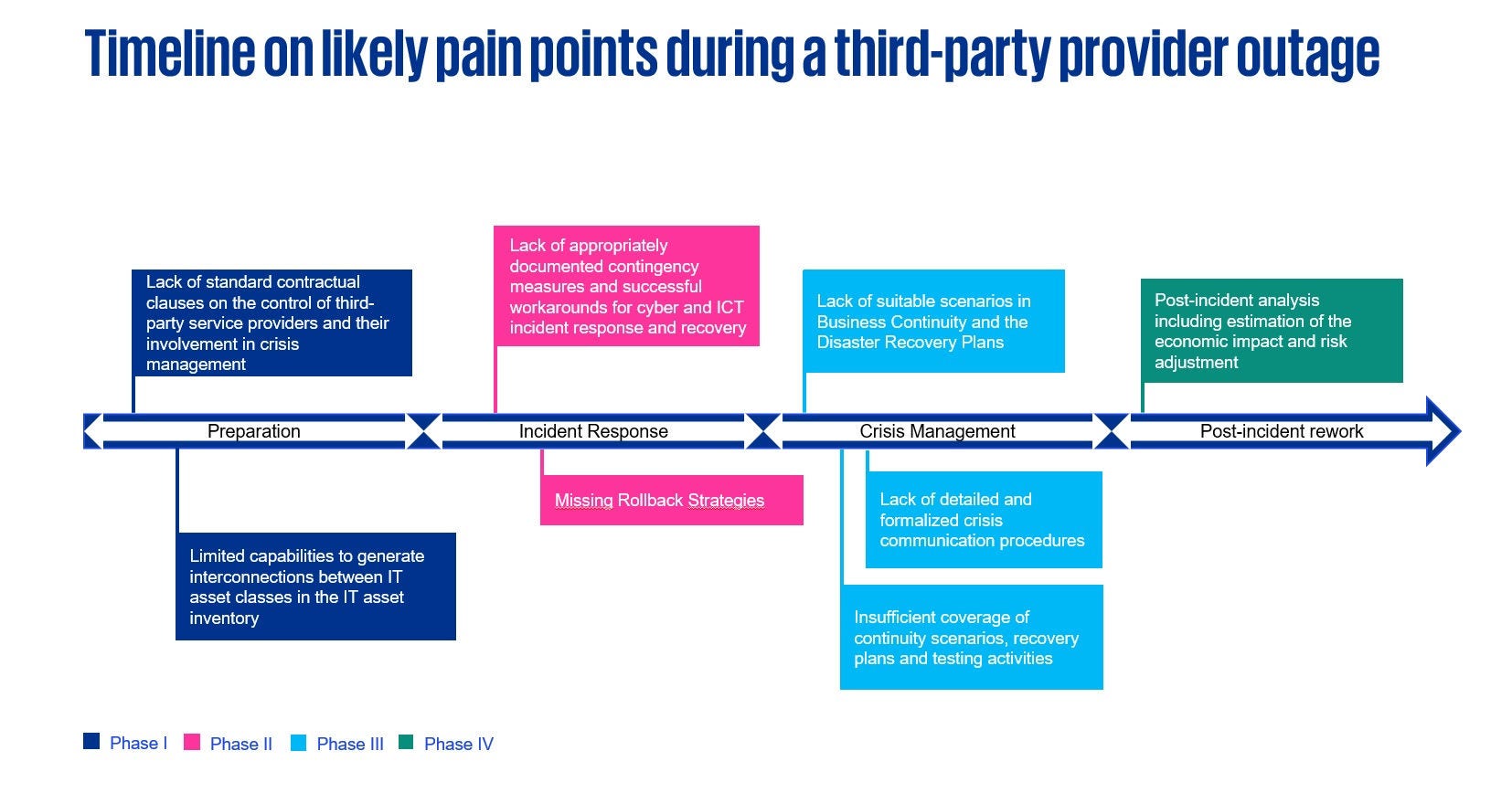
Source: KPMG International, 2024
With appropriate measures, banks can avoid these pain points.
Incident preparation: Adequate preparation for an emergency includes the following measures:
- Clear contractual clauses regarding service providers’ involvement in crisis management during cyber and ICT incidents.
- Thorough mapping of interconnections between different assets in the ICT inventory and links between process landscape and ICT infrastructure.
Incident response: Immediate responses to cyber and ICT incidents are commonly made more efficient by:
- Sufficiently documented contingency measures
- Adequate planning of feasible workarounds.
- Appropriate rollback strategies for successful recovery.
Crisis management: Banks’ ability to effectively recover from cyber-attacks and other critical incidents is typically enhanced by:
- The inclusion of suitable scenarios in both the Business Continuity Plan (BCP) and the Disaster Recovery Plan (DRP).
- Proper alignment with service providers over their responsibilities during the recovery phase.
- The establishment of detailed, formalised crisis communication procedures.
Post-incident reworking: The ability to learn from experience and improve cyber incident planning is often supported by:
- Strong post-incident analysis, evaluation and management reporting.
- Suitable approaches to estimating economic impact and risk adjustments.
DORA is not specifically aimed at preventing or mitigating third party failures like the disruption experienced in July. However, it does bring the most critical service providers for leading banks under the direct supervision of the European Supervisory Authorities (ESAs) — the European Banking Authority (EBA), European Insurance and Occupational Pensions Authority (EIOPA) and European Securities and Markets Authority (ESMA) — for the first time, and banks with a good level of DORA readiness should enjoy greater resilience to third-party outages. In this context, we see six key areas for banks to focus on as part of their DORA preparations:
No bank can predict when it will next become the target of a cyber-attack. But the frequency and severity of cyber incidents are only set to increase. Banks should act swiftly to strengthen their defences and upgrade their response plans to safeguard their resilience before trouble strikes.






