Modern managed services are moving from transactional to transformational. Cost saving is important, but we focus on innovation and automation to increase value and efficiency.
An end-to-end approach focused on innovation and modernization
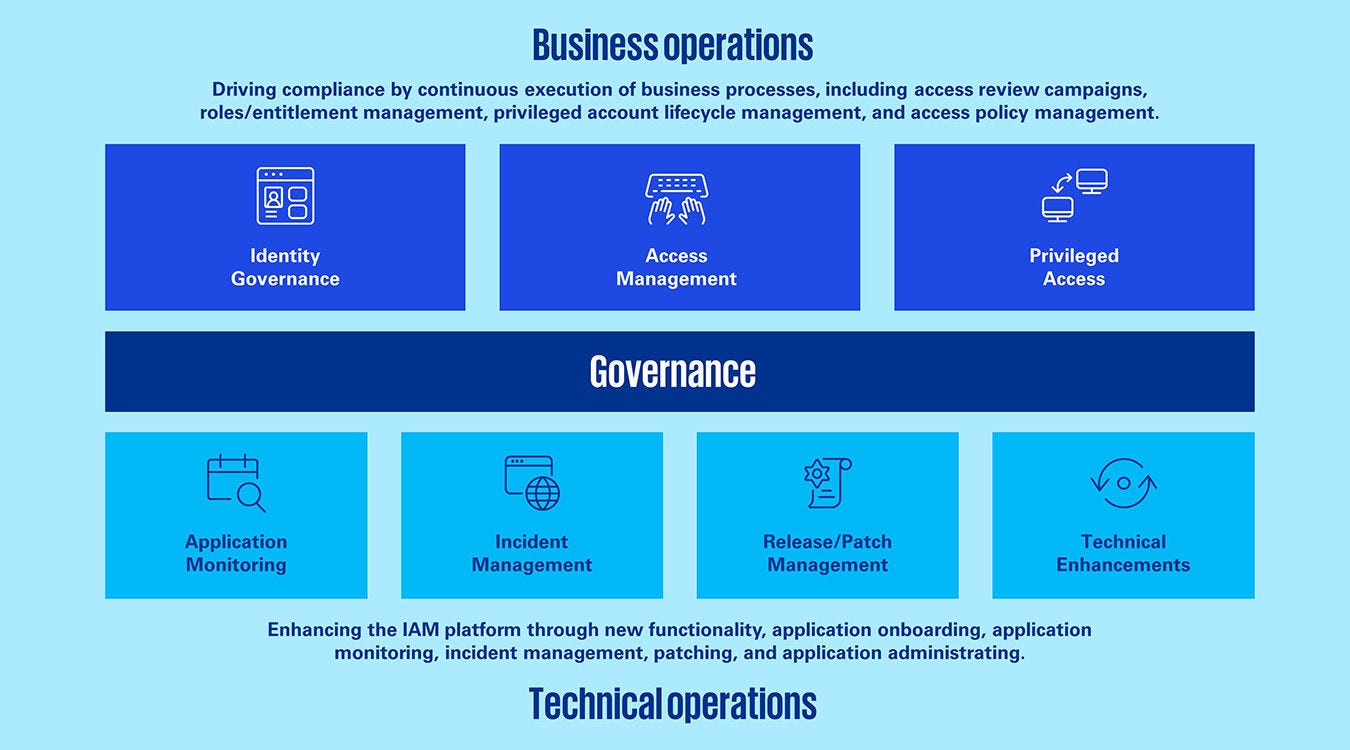
Our IAM solution offerings
- IAM Business Operations
- IAM Technical Operations
- Governance
- What our services are
IAM Business Operations
Continuous management and tracking of business processes, such as executing access review campaigns for SOX or access management for adding/removing access to applications, application onboarding, roles/entitlements management, privileged account lifecycle management and access policy management.
- Identity Governance: Orchestrating user privileges to ensure optimal security.
- Access Management: Managing user authentication and permissions to secure crucial system and data access.
- Privileged Access: Employing robust measures to protect sensitive credentials and deter unauthorized access
IAM Technical Operations
Daily management of IAM solution health such as application monitoring, data feed integrations, application administration and patching, and incident management.
- Application Monitoring: Real-time tracking for optimal application performance and reliability.
- Incident Management: Expedient resolution of technical disruptions for uninterrupted operations.
- Application/Account Onboarding: Onboarding of new applications/accounts on an ongoing basis for IAM solutions.
- Release Management: Administering timely updates and bug fixes for fortified system security.
- Technical Enhancements: Continuous administration, configuration, and enhancements of the IAM solution, including design, testing, and production deployment
Governance
Comprehensive IAM governance through offering reporting, quarterly business reviews, change management, and robust assessments/health checks for optimal identity management performance.
What our services are
- Outcome-based services tailored for agreed-upon businesses, objectives vest on demand, approaches, or time and materials.
- Capacity and skills focused to ensure you have the right resources at the right time.
- Continuously innovating to bring the latest technology and accelerators to optimize delivery
- Capability augmented so that you own the cyber function, but leverage our processes, choose an experience.
- Subscription-based and predictable monthly fees, while minimizing upfront costs.
Are you getting maximum benefit from your IAM technologies?
Cybersecurity identity and access management (IAM) technologies on their own can’t enable and protect your business. To maximize their benefits, you have to continue to expand the footprint, update the policies, and manage IAM operations over time.
Based on an established set of processes, policies, and integration patterns, KPMG Identity and Access Management On Demand helps you get the most out of your IAM investments. It includes user access review campaigns, application optimization and integration, and 24x7 monitoring, helping to elevate and extend your existing IAM solution.
Learn more:
Identity and Access Management On Demand
Explore more
Our people
Ron Walker
Global Head, Managed Services, KPMG International and Principal, Advisory
KPMG in the U.S.




